
College of Coastal Georgia Cyber Defense Students Continue to Impress in National Cyber League
College of Coastal Georgia cyber defense students were sailing with excitement at the end of Spring 2023 because of their performance at the bi-annual National Cyber League (NCL) competition. This year, Coastal moved up in ranking to 21 out of over 470 institutions, according to the Cyber Power Rankings. In Spring 2022, Coastal was ranked 75.
Every year, over 10,00 students from more than 500 colleges and universities, and 100 high schools in the United States, participate in the NCL competitions. The rankings represent the ability of students to perform real-world cybersecurity tasks on the Cyber Skyline platform. For the competition, students had to identify hackers from forensic data, perform pentests and audit vulnerable websites, recover from ransomware attacks, and more. Schools are ranked based on their top team performance, top student’s individual performance, and the combined individual performance of their students.
“Coastal Georgia is the highest ranked institution in Georgia,” said Associate Professor of Cyber Defense Dr. Nelbert “Doc” St. Clair. “NCL is the critical test of their skills, pitting them against cyber students from across the nation. The challenges are the same categories each competition, but the students are presented with different challenges each time. This makes research an important part of the learning process and the competition. I am very proud of the performance from the 33 cyber defense students.”
Spring 2023 Status:
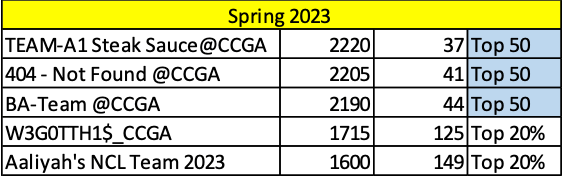
Three Coastal Georgia teams made the Top 50.
All five teams from the College made the Top 20% of the competition out of 968 teams.
The National Cyber League (NCL) is a cybersecurity competition that offers a variety of categories to challenge participants’ skills and knowledge in different aspects of cybersecurity. The NCL competition typically consists of the following categories:
1. Open Source Intelligence (OSINT): This category focuses on gathering information from publicly available sources on the internet to solve puzzles and challenges. Participants are required to use their investigative skills to find hidden information.
2. Cryptography: Cryptography challenges involve deciphering encrypted messages and understanding cryptographic principles. Participants need to have a strong grasp of encryption algorithms and techniques.
3. Password Cracking: In this category, participants attempt to crack passwords using various techniques, such as dictionary attacks, brute force attacks, and password hashing analysis.
4. Log Analysis: Log analysis challenges involve examining log files from various systems and identifying suspicious or malicious activities. Participants need to have a keen eye for anomalies and potential security breaches.
5. Network Traffic Analysis: This category requires participants to analyze network traffic captures to identify vulnerabilities, potential attacks, and other security issues within a network.
6. Forensics: Forensics challenges involve investigating digital artifacts, such as file systems, memory dumps, and network traffic, to uncover evidence related to cyber incidents. Participants must have strong forensic analysis skills.
7. Scanning and Reconnaissance: This category focuses on scanning and reconnaissance techniques, where participants need to gather information about target systems and identify potential vulnerabilities.
8. Web Application Exploitation: Participants are required to identify and exploit vulnerabilities in web applications, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
9. Enumeration and Exploitation: This category involves identifying and exploiting vulnerabilities in various operating systems and services, including Windows and Linux environments.
These categories encompass a wide range of cybersecurity skills, allowing participants to showcase their expertise in specific areas or develop a well-rounded skill set in the field of cybersecurity. Each category challenges participants to think critically, problem-solve, and apply their knowledge to real-world scenarios.